[ad_1]
OAuth apps used in cryptocurrency mining, phishing campaigns, and BEC attacks

Microsoft warns that threat actors are using OAuth applications cryptocurrency mining campaigns and phishing attacks.
Threat actors are using OAuth applications such as an automation tool in cryptocurrency mining campaigns and other financially motivated attacks.
The attackers compromise user accounts to create, modify, and grant high privileges to OAuth applications to carry out malicious activity and maintain access to applications even if they lose access to the initially compromised account.
Microsoft Threat Intelligence also observed threat actors launching phishing or password spraying attacks to compromise user accounts that did not have strong authentication mechanisms and had permissions to create or modify OAuth applications.
“The threat actors misused the OAuth applications with high privilege permissions to deploy virtual machines (VMs) for cryptocurrency mining, establish persistence following business email compromise (BEC), and launch spamming activity using the targeted organization’s resources and domain name.” states Microsoft.

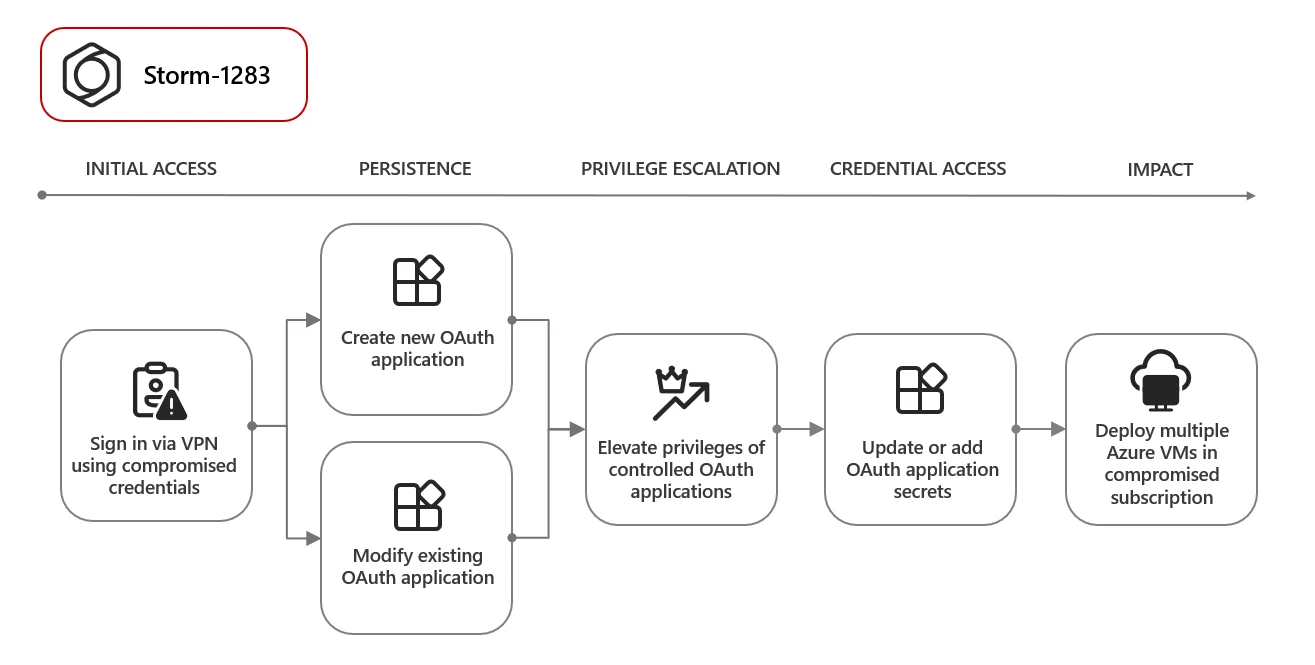
One of the threat actors that used compromised accounts to create OAuth applications is the Storm-1283 group. The compromised account allowed the attackers to create an OAuth application and deploy VMs as part of a cryptomining campaign.
“The compromised account allowed Storm-1283 to sign in via virtual private network (VPN), create a new single-tenant OAuth application in Microsoft Entra ID named similarly as the Microsoft Entra ID tenant domain name, and add a set of secrets to the application.” continues the report. “As the compromised account had an ownership role on an Azure subscription, the actor also granted ‘Contributor’ role permission for the application to one of the active subscriptions using the compromised account.”
The researchers observed the group using existing line-of-business (LOB) OAuth applications accessible to the compromised user account. They achieved this by adding an additional set of credentials to those applications.
Initially, Storm-1283 established a small number of virtual machines (VMs) within the compromised subscriptions, utilizing an existing application to carry out cryptomining activities. Subsequently, the threat actors used the compromised environment to add additional VMs using a novel application. The cryptomining activity financial losses ranging from 10,000 to 1.5 million USD to targeted organizations.
Microsoft observed a differed threat actor using compromised user accounts and creating OAuth applications to maintain persistence and to launch phishing attacks. The actor used an adversary-in-the-middle (AiTM) phishing kit targeting user accounts in multiple organizations.
Microsoft Threat Intelligence also observed a distinct actor leveraging the compromised user account to perform BEC financial fraud reconnaissance by opening email attachments in Microsoft Outlook Web Application (OWA). The actor looked at specific keywords, such as “payment” and “invoice,” in email attachments to gather intelligence on the targets.

Microsoft also observed another threat actor, tracked as Storm-1286, carrying out a large-scale spamming activity via OAuth applications.
Microsoft provided the following mitigations to reduce the impact of these types of threats:
- Mitigate credential guessing attacks risks;
- Enable conditional access policies;
- Ensure continuous access evaluation is enabled;
- Enable security defaults;
- Enable Microsoft Defender automatic attack disruption;
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, OAuth applications)
[ad_2]







Add comment