[ad_1]
Crowdfense is offering a larger 30M USD exploit acquisition program

Zero-day broker firm Crowdfense announced a 30 million USD offer as part of its Exploit Acquisition Program.
Crowdfense is a world-leading research hub and acquisition platform focused on high-quality zero-day exploits and advanced vulnerability research.
In 2019 the company made the headlines for its 10M USD bug bounty program along with its unique “Vulnerability Research Hub” (VRH) online platform.
Last week the company announced that they are offering up to 30M USD for their acquisition program. The firm is extending its scope to include other important research areas like Enterprise Software, WiFi/Baseband and Messengers.
Zero-day brokers acquire zero-day exploits to re-sell them to intelligence and law enforcement agencies or government contractors. The buyers claim to use the exploits to develop hacking tools used for this investigations.
Crowdfense is offering between $5 and $7 million for iPhone zero-day exploits, up to $5 million for zero-days to break into Android phones, up to $3 million and $3.5 million for Chrome and Safari zero-days respectively, and $3 to $5 million for WhatsApp and iMessage zero-days.
“This year, we are offering a larger 30M USD acquisition program, extending its scope to include other important research areas like Enterprise Software, WiFi/Baseband and Messengers.” reads the announcement published by the company. “Payouts for full-chains or previously unreported, exclusive capabilities, range from USD 10,000 to USD 9 million per successful submission. Partial chains will be evaluated on a case-by-case basis and priced proportionally.”

Crowdfense is also offering many other payouts for less sophisticated zero-day exploits targeting multiple products, including Chrome and Safari browsers.
In 2019 price list, the company offered $3 million for a zero-click remote code execution expploit for Android and iOS.
It is interesting to note that overall payouts offered by the company have increased since 2019 because vendors have improved the security of their products, making it harder to find zero-day flaws that can bypass implemented security measures.
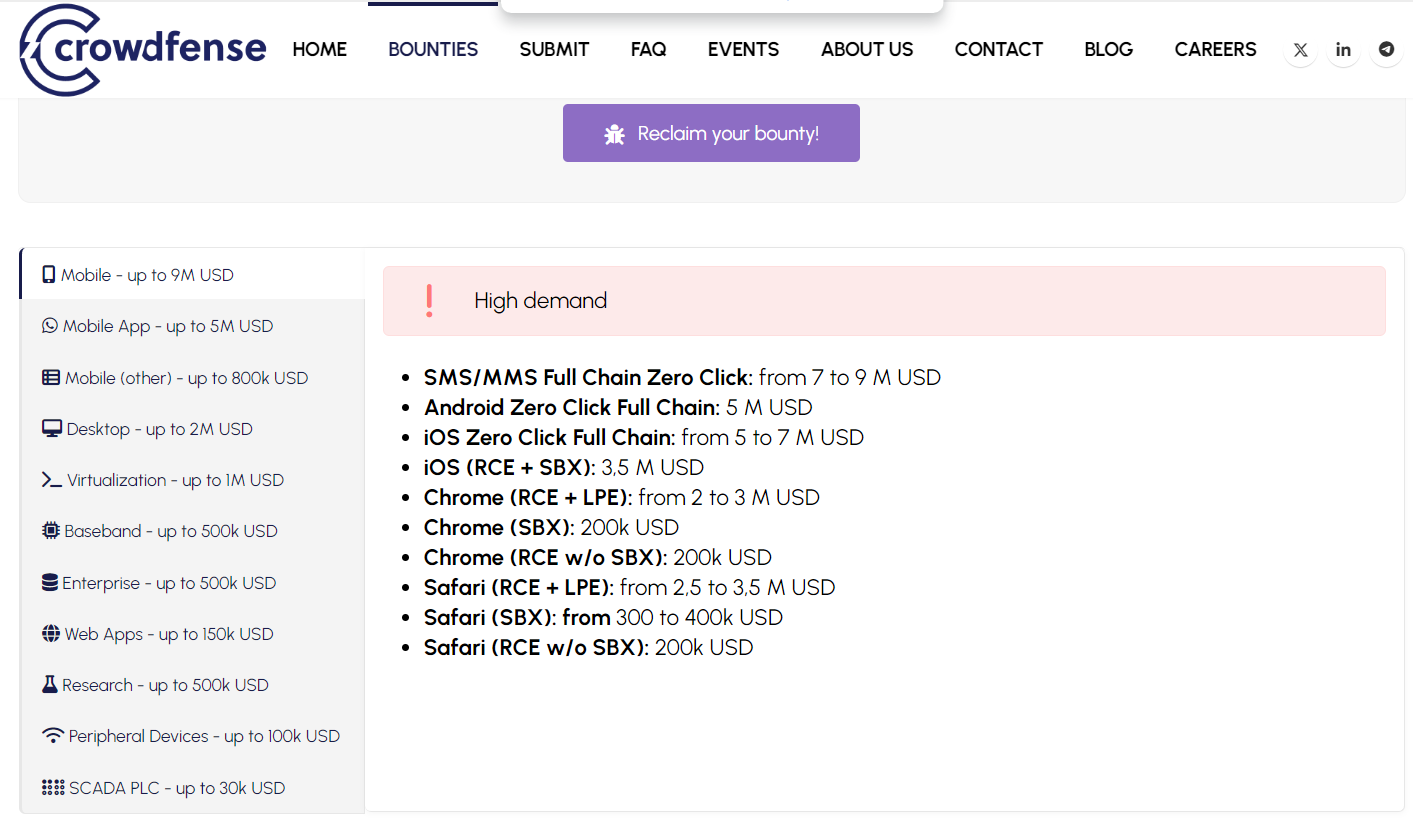
Below is the high demand bug bounties published by the company:
- SMS/MMS Full Chain Zero Click: from 7 to 9 M USD
- Android Zero Click Full Chain: 5 M USD
- iOS Zero Click Full Chain: from 5 to 7 M USD
- iOS (RCE + SBX): 3,5 M USD
- Chrome (RCE + LPE): from 2 to 3 M USD
- Chrome (SBX): 200k USD
- Chrome (RCE w/o SBX): 200k USD
- Safari (RCE + LPE): from 2,5 to 3,5 M USD
- Safari (SBX): from 300 to 400k USD
- Safari (RCE w/o SBX): 200k USD
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, zero-day exploit)
[ad_2]







Add comment